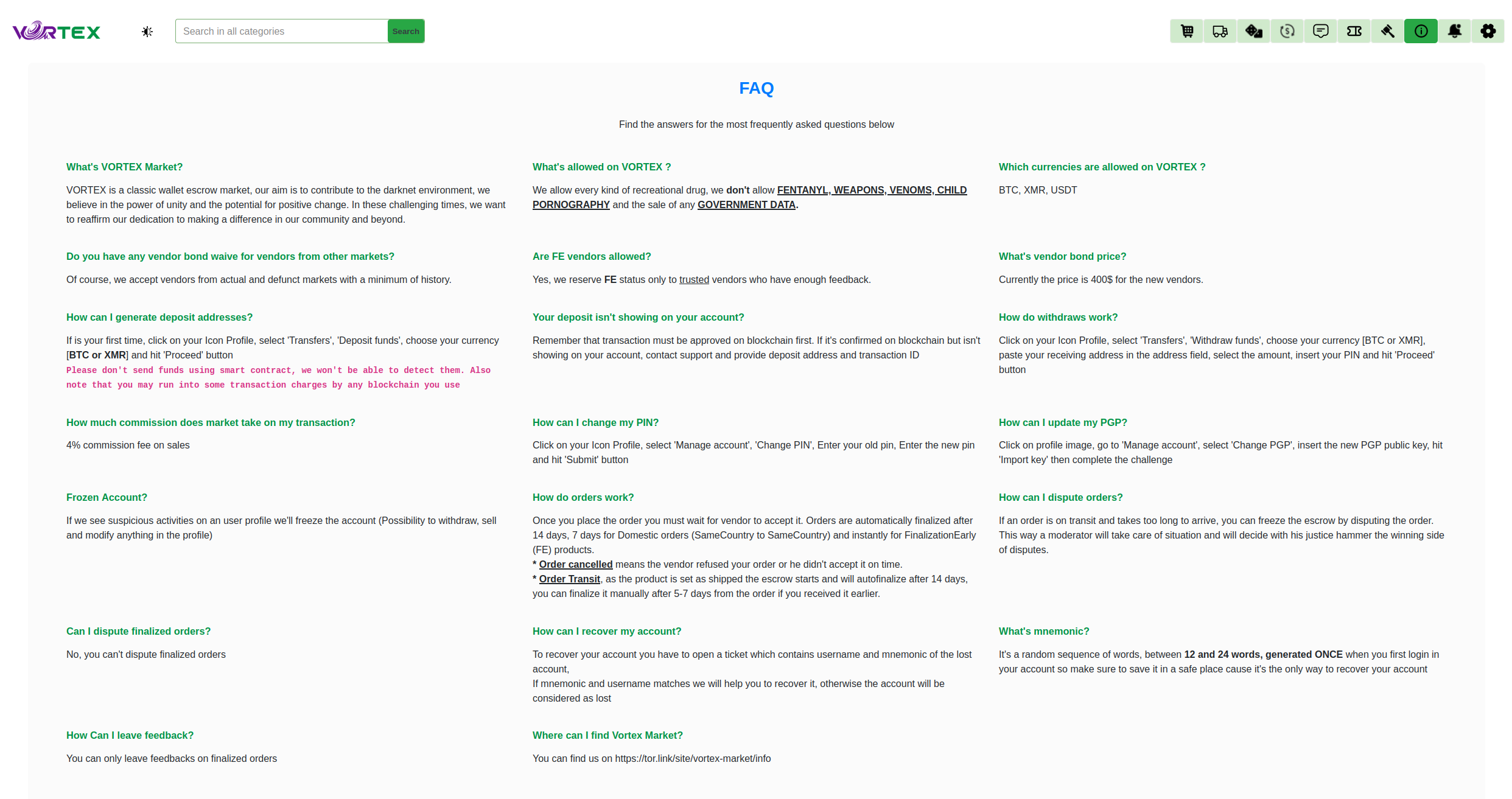
Vortex Market 2026: Official Onion Links & Verified Mirrors
Join the darknet’s most secure marketplace, where every transaction is sealed in layers of cryptographic ice and trust never melts. Welcome to the true frozen fortress of anonymity and commerce.